
|
Wireless Network |
|---|
|
The wireless network is that the nodes communicate without a wired infrastructure. There are several different technologies that are widely used for wireless communication: radio, infrared, and laser links. In common, radio interfaces are usually used in ad-hoc network since they can communicate without knowing where the other nodes are and do not need a clear line of sight. Wireless networks more difficult than traditional wired network. In a wired network, the transmitted data is confined to cables or fibers, and doesn’t usually cause any problems for others. However, in the case of radio communication by mobile nodes the data is transmitted with equal power in all directions and can be overheard by all others within range. Even those outside of the communication range are affected, since radio transmissions can be noticed farther away than they can be received. Therefore, wireless transmissions can not be thought to be very reliable. In the wireless case, transmission layer errors would be happened much more than one of the wired networks. There are many kinds of the radio technologies: IEEE 802.11, Bluetooth, TDMA, CDMA, FDMA and a multitude of experimental protocols designed for ad hoc networks. For more information on IEEE 802.11 standard, follow this link: http://www.ieee802.org/11/ |
|
IEEE 802.11 |
|
In IEEE's proposed standard for wireless LANs (IEEE 802.11), there are two different ways to configure a network: ad-hoc and infrastructure. In the ad-hoc network, computers are brought together to form a network "on the fly." As shown in Figure 1, there is no structure to the network; there are no fixed points; and usually every node is able to communicate with every other node. A good example of this is the aforementioned meeting where employees bring laptop computers together to communicate and share design or financial information. Although it seems that order would be difficult to maintain in this type of network, algorithms such as the spokesman election algorithm (SEA) have been designed to "elect" one machine as the base station (master) of the network with the others being slaves. Another algorithm in ad-hoc network architectures uses a broadcast and flooding method to all other nodes to establish who's who. As shown in Figure 2, the second type of network structure used in wireless LANs is the infrastructure. This architecture uses fixed network access points with which mobile nodes can communicate. These network access points are sometime connected to landlines to widen the LAN's capability by bridging wireless nodes to other wired nodes. If service areas overlap, handoffs can occur. This structure is very similar to the present day cellular networks around the world. For more information on IEEE 802.11 standard, follow this link: http://www.ieee802.org/11/ |
|
IEEE 802.11 Layers |
|
The IEEE 802.11 standard places specifications on the parameters of both the physical (PHY) and medium access control (MAC) layers of the network. The PHY layer, which actually handles the transmission of data between nodes, can use either direct sequence spread spectrum, frequency-hopping spread spectrum, or infrared (IR) pulse position modulation. IEEE 802.11 makes provisions for data rates of either 1 Mbps or 2 Mbps, and calls for operation in the 2.4 - 2.4835 GHz frequency band (in the case of spread-spectrum transmission), which is an unlicensed band for industrial, scientific, and medical (ISM) applications, and 300 - 428,000 GHz for IR transmission. Infrared is generally considered to be more secure to eavesdropping, because IR transmissions require absolute line-of-sight links (no transmission is possible outside any simply connected space or around corners), as opposed to radio frequency transmissions, which can penetrate walls and be intercepted by third parties unknowingly. However, infrared transmissions can be adversely affected by sunlight [5], and the spread-spectrum protocol of 802.11 does provide some rudimentary security for typical data transfers. The MAC layer is a set of protocols which is responsible for maintaining order in the use of a shared medium. The 802.11 standard specifies a carrier sense multiple access with collision avoidance (CSMA/CA) protocol. In this protocol, when a node receives a packet to be transmitted, it first listens to ensure no other node is transmitting. If the channel is clear, it then transmits the packet. Otherwise, it chooses a random "backoff factor" which determines the amount of time the node must wait until it is allowed to transmit its packet. During periods in which the channel is clear, the transmitting node decrements its backoff counter. (When the channel is busy it does not decrement its backoff counter.) When the backoff counter reaches zero, the node transmits the packet. Since the probability that two nodes will choose the same backoff factor is small, collisions between packets are minimized. Collision detection, as is employed in Ethernet, cannot be used for the radio frequency transmissions of IEEE 802.11. The reason for this is that when a node is transmitting it cannot hear any other node in the system which may be transmitting, since its own signal will drown out any others arriving at the node. 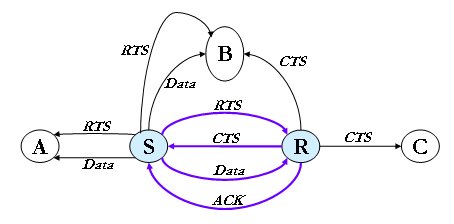
Whenever a packet is to be transmitted, the transmitting node first sends out a short ready-to-send (RTS) packet containing information on the length of the packet. If the receiving node hears the RTS, it responds with a short clear-to-send (CTS) packet. After this exchange, the transmitting node sends its packet. When the packet is received successfully, as determined by a cyclic redundancy check (CRC), the receiving node transmits an acknowledgment (ACK) packet. This back-and-forth exchange is necessary to avoid the "hidden node" problem, illustrated in Figure 3. As shown, node A can communicate with node B, and node B can communicate with node C. However, node A cannot communicate node C. Thus, for instance, although node A may sense the channel to be clear, node C may in fact be transmitting to node B. The protocol described above alerts node A that node B is busy, and hence it must wait before transmitting its packet. For more information on IEEE 802.11 standard, follow this link: http://www.ieee802.org/11/ |

Copyright(c) 2002. All rights reserved.
faithink@bu.edu,
kimsooil@bu.edu