

Freenet is a decentralized, scalable peer-to-peer application allowing anonymity to the publisher, requestor and storer of files. While Chord is a seach protocol as a basis for future peer-to-peer applications, Freenet is a complete application supporting file caching and other features to guarantee a user's anonimity. However, unlike Chord, Freenet does not guarantee that a query will return a specific document that exist on the network.
Each document on the Freenet network is assigned a hash key based on the file's descriptive name. Each node contains a table of the keys associated with the documents it possesses. In addition, Freenet nodes maintain a table of information about neighboring nodes and the keys it suspects them of holding. This is different from Chord where keys are assigned to specific nodes. By eliminating the relationship between node identifiers and keys, the anonimity of the storer is maintained.
When a node is queried
for a document not found in its finger table, the query will be forwarded to
the node which is suspected of containing documents with similar keys. A simplified
example is used to illustrate this point. Table 1 shows data that is stored
by an imaginary node A. Node A hold 4 files with keys 2, 12, 16 and 32. In addition,
node A suspects that its neighboring node B holds the document associated with
key 14, node C holds 2 documents associated with keys 18 and 25 and node D possesses
the document associated with key 87. If node A received a query for key 78,
since it does not have key 78 in its store or in its routing table, the query
would be sent to the node with the closest key, or node D in this example.
|
|
Freenet makes use of an aggressive caching scheme. When a document is found, it can be cached at multiple points along the path between the request and the point where the document is located. This can speed up future request for the same document. In order to protect the identity of the requestor, nodes along the path to the document can identify themselves as the node that requested the file, then forward the document on to the node sending the original request. To protect the identity of the storer, a similar process takes place where a node along the path will claim to be the original storer of the document.
Freenet
queries make use of a depth-first search with a configurable time-to-live (TTL).
A typical query is illustrated in Figure 1. An interesting aspect of Freenet
is how the TTL decrements. For example, if a request starts with a TTL=7 at
node A in Figure 1, at node B, the TTL would be decremented to 6. When the request
is forwarded to node C, again the TTL would be decremented to 5. However, since
node C is a dead-end, the search would back out to node B, a continue from there
with a TTL of 6.
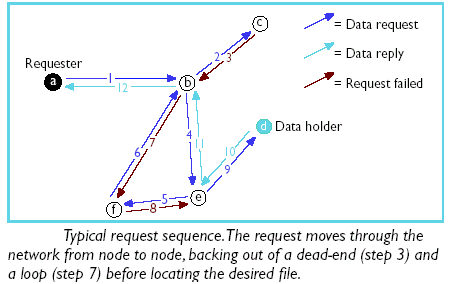
Figure 1