
Concerns with Mobile IP
Problems that Mobile IP Solves

Before discussing the concerns with Mobile IP, we should first re-cap the problems Mobile IP solves:
*When a node moved from one node to another, it’s IP address changes and will be able to receive packets at a new link
*When the node moves and changes its IP address, it will not have to terminate and restart any ongoing actions each time it moves
The above demonstrates that Mobile IP has the possibility to be promising for the future, solving these problems in a vigorous and medium-independent manner. Its scaling properties make it pertinent throughout the entire Internet.
Currently, its outlook is unclear. The current IPv4 is a good base for the potential of Mobile IP. There are many problems facing Mobile IP, many with future and in-the-making solutions, which IPv6 hopes to implement.
Security Issues

The most outstanding problem with Mobile IP is security. A computer’s resources and information must be protected from unauthorized admission, variation, and damage. Security involves several factors.
*Data must be transformed so that authorized parties only decode it
*Authentication, or approving or disproving someone’s identity
*Ensuring that data cannot be changed without having that change be detectable
*Proving a source sent data and the possibility of that data being denied
Achievement of Security Factors
To ensure the above security factors, a system composed of a mathematical algorithm and a secret or public key. A key is defined as a string of binary digits known to only users who want to communicate securely. The algorithm can either be secret or public key. A public key algorithm uses a duo of related keys, one by the sender, and the other one by the receiver. One of the keys in the pair is kept secret or private, while the other is published publicly. These algorithms are generally used to provide confidentiality.
Secret-key and public-key is used for authentication. Secret-key can be separated into two categories. The first is constructed from the same algorithms that are used to implement secret-key, as described above. The second uses algorithms known as message digests. Message-digest algorithms make use of a large piece of data and calculate a fixed-length piece of data called a message digest. Similarly, public-key authentication also falls into two categories. Public-key executes the same as secret-key, with the exception of using secret-key encryption. The second type of public-key authentication uses digital signatures. A digital signature requires simply changing public-key to a plaintext message, using the private key. This is called signing the message, and the result is called a digital signature. Digital signatures also do not refute anyone since only the sender has the key. To validate that a message has not been changed during transmission, the sender sends a message, a timestamp, and a message digest.
Firewalls

Firewalls cause complexity for Mobile IP because they block all classes of incoming packets that don’t meet certain criteria. A firewall is a device that separates a trusted, private network from a public network, like the Internet. This may have an advantage of managing internal Internet nodes, without a great amount of security, but a disadvantage of preventing internal mobile nodes from communicating with other nodes within their home networks.
There are three types of Firewalls:
1) Packet-filtering router: decides whether to forward a certain packet by looking at the packet’s header by following a certain set of rules.
2) Application-layer relays: buffer between the host and the public network where routers do not permit packets to run directly between the host network and the public network.
3) Secure tunneler: supplies a cryptographically secure process for authorized users to access a private network through a public network.
Security Threats to Mobile IP

Insider Attacks
Example: an employee within a company gaining access to confidential data and forwarding information to outside source
Possible solution: enforcing strict control of who can access data; authentication of users and computers; encode data to source and destination to prevent eavesdropping
Denial of Service Attack (DOS)
Example: User floods with nuisance packets so that no one can accomplish their tasks (TCP SYN flooding)
Possible solution: Not much can be done for a flood, but providers can filter IP packets in their routers to make sure that the source address is authentic before it is forwarded.
Replay Attacks
Example: An attacker gets a copy of a legitimate Registration Request, store it, andre-use it. Consequently, the attacker can register a synthetic care-of address for the mobile node
Possible solution: Mobile node producing a unique ID field in each successive attempt for registration. The ID field allows the home agent to find out what the following value should be. The attacker is disadvantaged because the ID field in his stored Registration Request will be outdated according to the home agent.
Theft of Information: Passive Eavesdropping

Example: Attacker targets confidentiality of information.
Possible Solutions:
Two ways to protect data from unauthorized users:
1) End-to-end encryption: encoding and decoding information at the source and destination instead of over first and last link. Examples:
2) Link layer encryption: used between mobile node and foreign agent of wireless link. In this case, the mobile node and the foreign agent encrypt all packets they trade over the foreign link. It is particularly useful when dealing with wireless LAN. It is easier to attack a wireless link because no physical connection is required.
Theft of Information: Session-Stealing

Example: Attacker waits for a node to validate itself and initiate an application session then captures the session, posing as the rightful node.
Possible Solutions: This type of attack involves transmitting various nuisance packets to prevent the legitimate node from recognizing that the session has been captured. The attack can be prevented from the above actions, end-to-end and link layer encryptions.
Route Optimization: Triangle Routing Problem

Although the most outstanding problem facing Mobile IP is security, other technical obstacles to deployment exist. Perhaps the second largest problem of Mobile IP is Triangle Routing.
The basic idea behind triangle routing is as follows. A mobile node wants send a packet to another node that is on the same network. The receiver node happens to be the far side of the Internet, far away from the mobile node’s home network. Then the sending node addresses all the packets to the home network. They pass through the Internet to reach the home agent and then tunnels them back across the Internet to reach the foreign agent. It would be optimal if the sending node could find out that the mobile node is on the same network and deliver the packet directly. In more general terms, the goal is to deliver packets as directly as possible from sending node to mobile node without passing through a home agent. This scheme is called triangle routing because the single “leg” of the triangle goes from a mobile node to the corresponding node, and the home agent forms the third vertex, controlling the path taken by the data from the correspondent node to the mobile node. This is obviously a problem since route from sender to mobile node by way of the home agent takes two sides of the triangle, rather than the third side, which is the direct path.
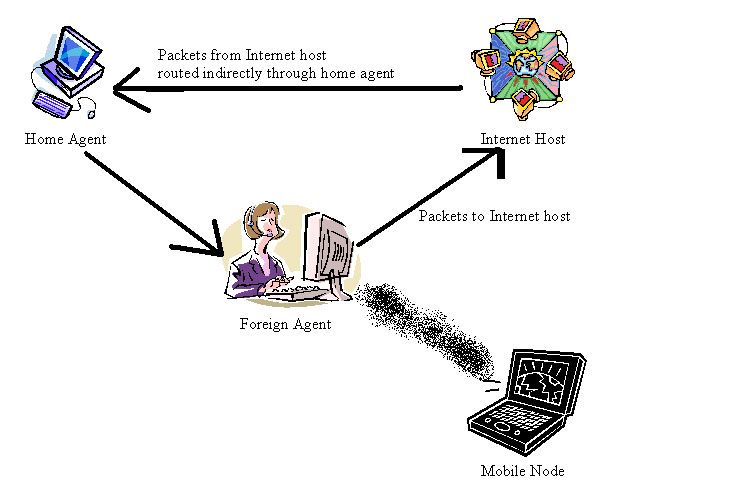
The Solution
Triangle routing problem delays the delivery of the datagrams to mobile nodes and places an unnecessary burden on networks and routers along their paths through the Internet. This all can be improved by techniques in the route optimization, delivery of packets directly to care-of address from a correspondent node without having to detour through the home network. The sending node should be “told” the care-of address of the mobile node. The sending node makes its own tunnel to the foreign agent, an optimization of the process that was aforementioned. In the case where the sender contains the required software to learn the care-of address and is able to create its own tunnel, then the route is optimized. If not, another route must obviously be taken.
A home agent finds out that a packet is being sent from one of the mobile nodes that it supports. From here, the home agent is aware that the sender is not using the optimal route. It then sends a “binding update” message back to the source as well as forwarding the packet back to the foreign agent. The source then uses this information, if proficient, to construct an entry in the “binding cache”. This binding cache is a “book” of mappings from mobile node addresses and care-of addresses. The next time this source has a packet to send to that mobile node, it will find the section in the cache and will tunnel the packet directly to the foreign agent.
The Problem with the Solution
Although the solution seems efficient, the route optimization scheme contains an obvious problem. When the mobile host moves to a new network, the binding cache may become outdated. If this outdated entry is utilized, the foreign agent will receive tunneled packets that are no longer registered with the network. In the event of this occurring, a “binding warning” is sent to the sender to advise it to stop using the cache entry. This will only work if the foreign agent is not the mobile node itself. Knowing this information, cache entries should be deleted after time has passed.
Other Issues

Some other issues are faced in Mobile IP. One concerns the perception of reliability, which refers to the premise of Mobile IP connections are based on TCP surviving cell changes. Many people assume that most communication systems are bursty and an increase in reliability is not needed. Another concern regards issues in IP addressing. Mobile IP creates a perception that a mobile node is always attached to its home network. Inefficiencies can branch from this. For example, many of communications are short lived and don’t depend on the identity of the node, this does not take advantage of the idea of having a mobile node home address.
Lastly, the market plays a huge role in the growth of Mobile IP. Mobile IP has been introduced as a solution to wireless LAN location management and communications, but the market has been slow to develop. There is no specific reason for this slow progress, but faster wireless access over the standardized MAC layers could change this slow growth tremendously of this wireless LAN market. As expected, competition exists from other protocols as well. Other tunneling protocols offer portability to mobile computers. This idea may currently be striking, but this type of operation is not very ideal long term.